
Phish, Phish, Phish ...
Social engineering is the most common threat companies and individuals alike face. Malicious actors launch social engineering attacks in an attempt to gain access to information they can further exploit. There are several social engineering attacks such as Baiting, Pretexting, Quid Pro Quo, Phishing, etc. So, which social engineering attack is most commonly used? Phishing! That’s right, phishing has a high success rate making it a favorite among malicious actors. But how effective are we at detecting phishing emails? Well, the answer is … we are not as effective as we like to think. Even cybersecurity professionals have fallen victim to phishing attacks!
Hooking The Bait ...
Malicious actors have a way of making their phishing emails sound important and urgent. They hook the victim by making them think that they must take action and if not there will be a negative consequence in return. Phishing emails will usually contain a malicious link or attachment.
Let's look at the following email ...
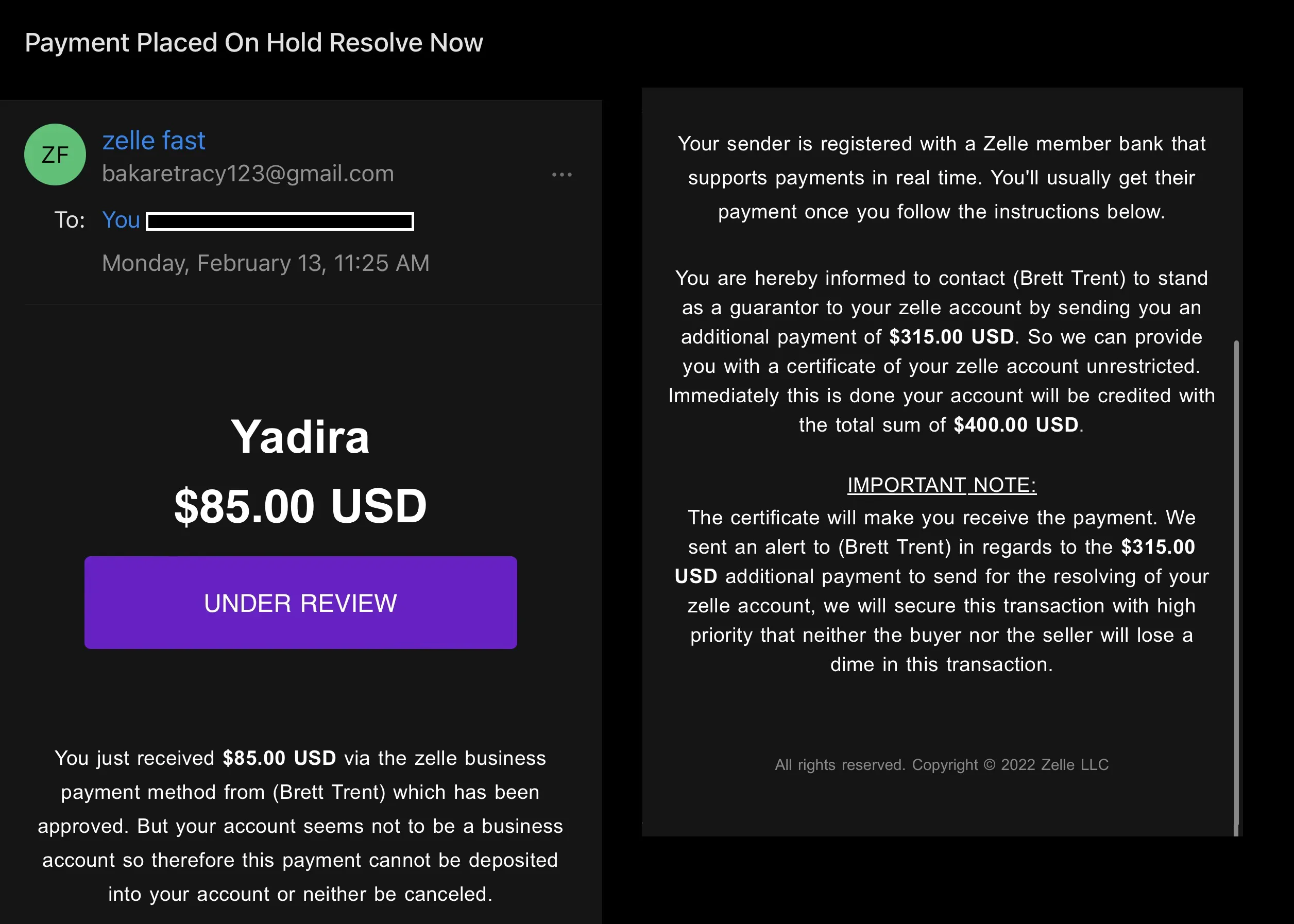
... Do you spot any red flags?
Although phishing emails vary in content, they all tend to contain the same red flags. Let's examine the above email in detail ...

The subject line of this email suggests that the contents of the email are important and action must be taken. To be fair sometimes providers do send emails with subjects similar to this one. But it is important to note the sense of urgency the malicious actor is implementing here as it sets the tone for the rest of the email.
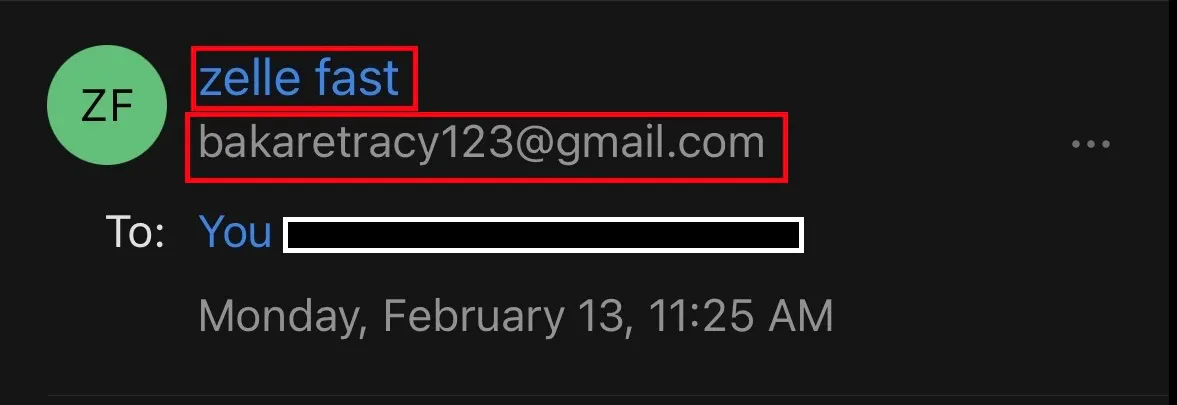
Next, take a look at the sender's name and email address. This is the first clear red flag encountered in this email. The sender's name indicates that this email should be coming from Zelle® but the name is zelle fast and the email address is bakaretracy123@gmail.com which shows that this email is not coming from Zelle® but rather from someone attempting to impersonate the company. Why would a legitimate company use a regular Gmail account to send its customers emails?
Phishy ...

The UNDER REVIEW purple button is clickable although at first glance it does not show any indication that it is. If the victim of this email had clicked on the button, they would have been taken to a website that prompts them to input their login credentials. Many times, malicious actors will include buttons like these to trick the victim into clicking it either out of curiosity or accidentally.
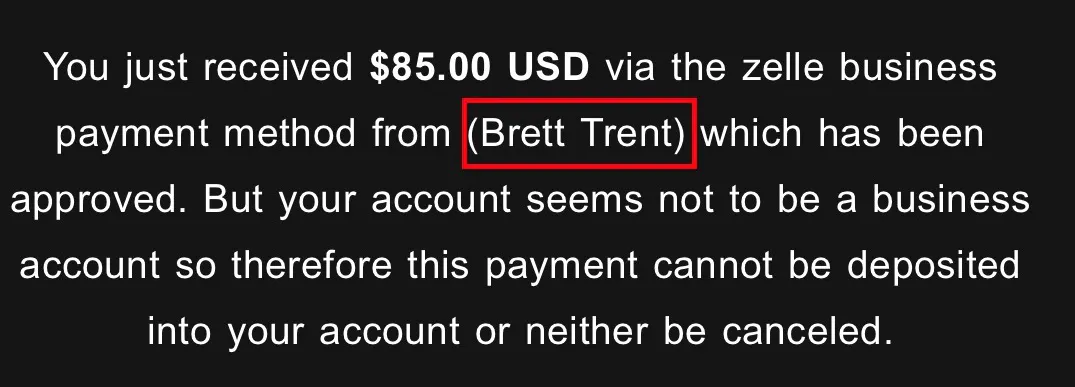
Upon further inspecting the body of the email many red flags can be spotted. The name of the person who is "sending" money is inside parentheses which is unusual. Malicious actors tend to use phishing templates for a faster creation process which contain fill-in fields and we can assume that they placed the name Brett Trent as one of the fillers.

The second paragraph also urges the victim to take action in order to receive payment by following the given instructions. It also fails to mention the name of the sender's bank. Another thing to note here is the use of the word usually which hints at a may or may not meaning.
"You'll may or may not get their payment once you follow the instructions below."
Smells real phishy ...

Again, pay attention to word usage. Here the malicious actor used the word hereby to sound authoritative. At the beginning of the email, there is an amount of $85 USD shown but, in this paragraph, it is stated that the victim will receive an additional $315.00 USD in order to obtain a certificate that provides an unrestricted zelle account. The malicious actor is promising more money than expected plus an unrestricted account, sounds too good to be true. The last sentence contains incorrect grammar which is typical for phishing emails. Grammar mistakes are not spotted right away and can be easily missed if not read thoroughly.
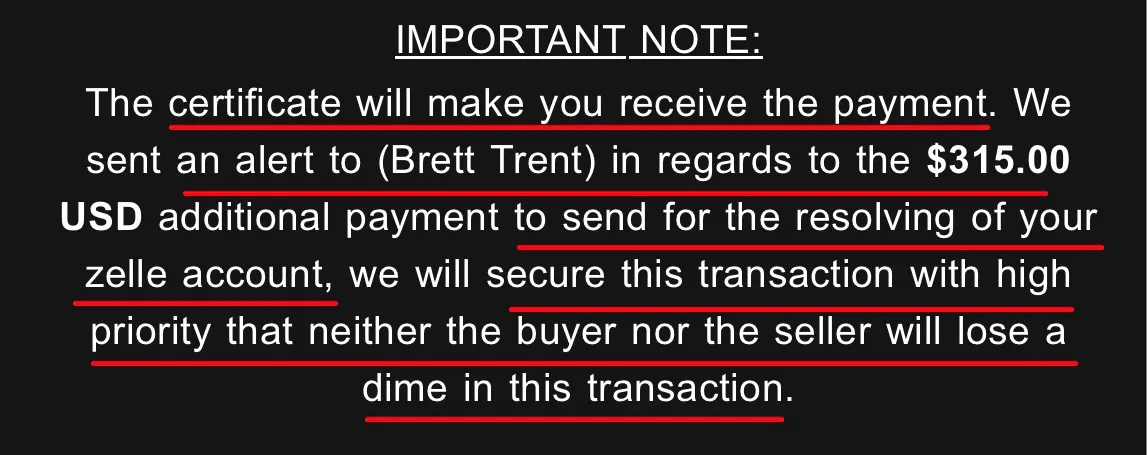
The malicious actor uses persuasive language to put the victim at ease and ensure them that they will receive their payment and an unrestricted zelle account. But hold on! They finish off by stating "neither the buyer nor the seller will lose a dime", this is an odd statement to make. I have not come across a company that uses language like this.
Lastly, at the end of the email, the malicious actor added a copyright stamp to further legitimatize the email. The legitimate Zelle® has the trademark symbol and it is owned by Early Warning Services, LLC.
Spotting The Phish ...
Here are the main takeaways to help spot phishing emails:
Email address - Pay attention to the structure of the email address and the sender's name. Often the name will look legitimate, but the email address will contain an error and give it away.
Tone & Timing - Malicious actors are notorious for setting a tone of urgency on their email subject lines and email bodies. If an email is prompting you to take action make sure you are expecting such email and if not, it is best to call your provider directly to verify.
Color scheme & graphics - If the email contains any graphics such as logos pay close attention to them as they will often seem a bit off (pixelated) and the color scheme will not match the actual legitimate company. This might not always be the case since some phishing emails are more sophisticated than others.
Grammar - This is probably one of the best things to look for because 9/10 times the phishing email contains misspelled words, improper sentence structure, slang, etc. However often these errors are overlooked because most people just skim through the email instead of reading it thoroughly.
Too good to be true offers - Some phishing emails will promise something in return for doing what is being asked of them but the reward sounds too good to be true. No one gives away money via email ... yea I know bummer.
Greeting - Phishing emails will contain a generalized greeting such as Hello Customer or Dear Customer. This is because malicious actors do not know your name or as explained earlier they are using fill-in phishing templates. Any service provider you use will always greet you by your first name or last name or both.
Attachments & Links - Be on the lookout for weird attachments and links since these can be malicious. Malicious attachments will have the file extension ending in something unfamiliar like .exe.
Requesting sensitive data - Credentials, financial information, and any Personal Identifiable Information (PII) are considered sensitive data. If an email is asking you to verify or provide sensitive data it is most likely a phishing email.
Phish Me Not ...
As technology evolves so do social engineering attacks and phishing emails are getting more sophisticated every day. Staying informed about phishing email trends and learning more about social engineering can save you from becoming a victim. Successful phishing attacks can cause devastating damage to companies and individuals. Data has become one of the most valuable assets that must be protected. Stay vigilant and say phish me not to malicious actors.